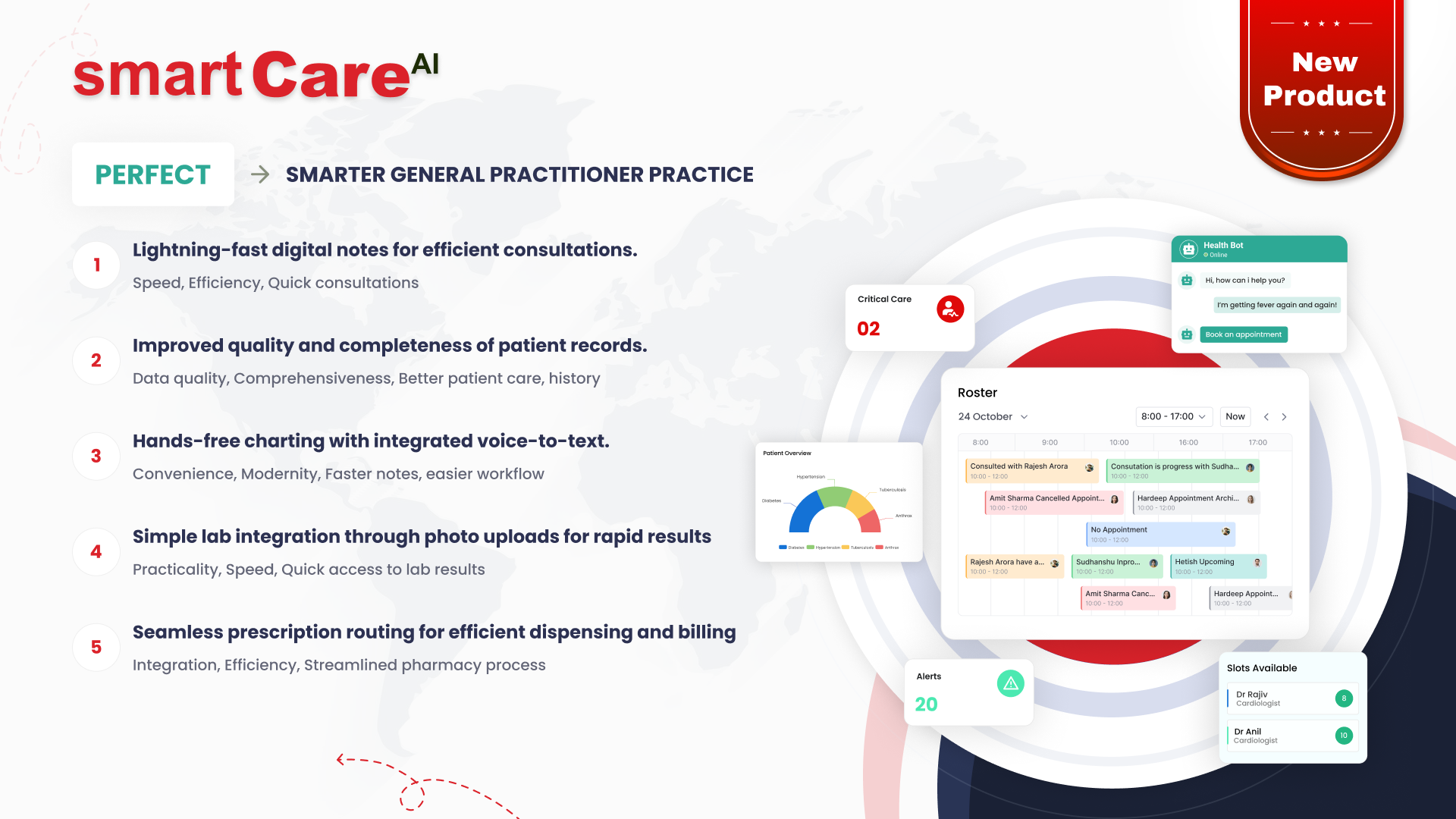
Posted On March 10, 2025
Top Security Challenges in Healthcare Software Development
Healthcare software development comes with numerous security challenges due to the sensitive nature of patient data. As digital transformation accelerates in the healthcare sector, ensuring robust security measures is critical. Here are some of the biggest security concerns healthcare software developers face:
Why Data Privacy Is a Major Concern in Healthcare Software
Patient records contain highly sensitive personal and medical information, making them a prime target for cybercriminals. Data privacy regulations, such as HIPAA (Health Insurance Portability and Accountability Act) in the U.S. and GDPR (General Data Protection Regulation) in Europe, mandate strict compliance measures to protect patient confidentiality. However, ensuring that healthcare software meets these regulatory standards can be complex, requiring encryption, access controls, and regular audits.
How Cyberattacks Threaten Patient Information Security
Healthcare organisations have become prime targets for cyberattacks, including ransomware, phishing, and malware. Hackers exploit vulnerabilities in outdated software, weak passwords, and unprotected systems to gain unauthorised access to patient data. A single breach can lead to massive financial losses, legal consequences, and a loss of trust among patients. Developers must prioritise security-first design principles and implement proactive monitoring solutions to detect and prevent attacks.
The Role of Compliance in Protecting Healthcare Data
Regulatory compliance is crucial in healthcare software development, as it ensures that organisations follow established data protection standards. Failure to comply with regulations can result in severe penalties and data breaches. Software developers must integrate compliance requirements into their development lifecycle, such as role-based access controls, secure data transmission protocols, and automated compliance monitoring. Keeping up with evolving regulatory landscapes is essential to maintaining data security.
Challenges in Securing Cloud-Based Healthcare Solutions
Cloud-based healthcare solutions offer scalability, flexibility, and cost efficiency, but they also introduce new security risks. Storing patient data on the cloud increases the risk of unauthorised access and data leakage. Developers must implement strong encryption, multi-factor authentication, and continuous monitoring to ensure data security in the cloud. Partnering with trusted cloud service providers that comply with healthcare regulations is also vital in mitigating security risks.
Why Insider Threats Are a Growing Risk in Healthcare IT
While external cyber threats pose a significant risk, insider threats are equally dangerous. Employees with access to sensitive data can misuse their privileges, either intentionally or accidentally. Unauthorised access, data leaks, and human errors can lead to compliance violations and security breaches. Implementing strict access controls, regular employee training, and real-time activity monitoring can help mitigate insider threats and safeguard patient information.
How Outdated Software Increases Security Vulnerabilities
Many healthcare organisations continue to use outdated systems that lack modern security features. Legacy software often does not receive regular updates, making it an easy target for cybercriminals. Without timely patches, vulnerabilities can be exploited, leading to data breaches and system failures. Regular updates and timely system migrations to newer, more secure platforms can help reduce risks.
The Importance of Secure Patient Authentication Methods
Weak authentication systems pose a major threat to healthcare security. Many breaches occur due to weak or compromised passwords. Implementing strong authentication measures such as multi-factor authentication (MFA), biometric verification, and encrypted login credentials can significantly enhance security. These measures ensure that only authorised personnel have access to sensitive patient information.
Managing Third-Party Risks in Healthcare Software Development
Many healthcare providers integrate third-party applications and services into their systems. However, these external vendors can introduce security vulnerabilities if they do not follow strict data protection protocols. Conducting thorough security assessments, establishing strong vendor agreements, and implementing regular audits can help manage third-party risks effectively.
Why Encryption Is Essential for Protecting Medical Records
Encryption is a fundamental security measure for safeguarding patient data. Without proper encryption, sensitive medical records can be exposed to cyber threats, including hacking and data theft. End-to-end encryption, both in transit and at rest, ensures that patient data remains protected from unauthorised access, reducing the risk of breaches and compliance violations.
How AI and Automation Help Strengthen Healthcare Cybersecurity
Artificial Intelligence (AI) and automation play a growing role in healthcare cybersecurity. AI-driven security systems can detect unusual activity and potential threats in real time, allowing for a quicker response to cyber incidents. Automation also helps in streamlining security protocols, ensuring compliance with industry standards, and reducing the risk of human error in data protection efforts.
Conclusion
As healthcare software continues to evolve, security challenges remain a top priority for developers and healthcare providers. Addressing data privacy concerns, defending against cyberattacks, ensuring regulatory compliance, securing cloud-based solutions, and mitigating insider threats are crucial steps in building a robust security framework. By adopting best practices and staying ahead of emerging threats, healthcare organisations can protect patient data and maintain trust in digital health solutions.
For more insights on secure healthcare software development, visit smartdatainc.com.